Operating systems (OS) have a support period, and when this period ends, security risks increase.
Especially with Windows OS, continuing to use a version after its support period has ended is very dangerous.
- Even after the support period ends, computers do not become unusable
- When the OS support period ends, security risks increase
- The best countermeasure is to upgrade to the latest OS as soon as possible
- Ideally, upgrade before the support period ends
- For companies, this can lead to serious security incidents such as customer information leaks
This article also explains the overall aspects of operating systems, such as types of OS, versions and editions, types of installation media, and license types.
≫ Related article: How to Choose an OS for a Custom PC [Performance / Features / Compatibility]
Select PC parts and online stores to instantly generate an estimate, check compatibility, and calculate power requirements. You can save up to five different builds, making it easy to try out multiple configurations.
≫ Tool:PC Parts Estimation & Compatibility Check Tool
Table of Contents
About OS Support Periods
This section explains about the support periods for operating systems.
Operating Systems Have a Set Support Period
Operating systems have a fixed period during which they receive support from the developer.
During this period, the developer provides updates such as adding or improving features, enhancing performance, improving the user interface, distributing security patches, fixing bugs, and updating compatibility so that the OS can be used more conveniently and safely.
A security patch is an update that fixes newly discovered security vulnerabilities, which helps protect the system from malicious attacks.
For Windows OS, updates are automatically applied through the Windows Update feature.
Generally, new operating systems are released every few years, so developers cannot continue to maintain old OS versions forever.
Therefore, these support periods are set, and once the period ends, updates and support for that OS are discontinued.
In other words, no more feature additions, improvements, or security updates will be provided.
Unsupported OS Versions Have Security Risks
When OS support ends, security updates from the developer are no longer provided.
As a result, newly discovered vulnerabilities and security holes are not fixed, making it easier for malicious attackers to target the system.
For example, viruses and malware can more easily enter the system, increasing the risk of serious damage such as personal information leaks or data destruction.
Furthermore, using an unsupported OS can negatively affect the security of the entire network, spreading risks to other computers and systems.
Therefore, it is important to upgrade to the latest OS before the support period ends.
In some cases, if a critical vulnerability is discovered, a security patch may be distributed for an unsupported OS as an exceptional measure.
If a security patch is distributed after support has ended, it indicates a significant risk, so be sure to update.
OS Can Still Be Used After Support Ends
Just because the support period has ended does not mean the OS will stop working.
You can still start up your computer and work as usual, so if you are worried that “the OS will stop working as soon as support ends,” you can rest assured.
However, vulnerabilities and security holes found after the support period will not be fixed.
Therefore, if these are exploited, it can lead to security incidents such as data leaks or corruption, so it is strongly recommended to upgrade to a new OS as soon as possible.
Countermeasure for End of Support: Upgrade to the Latest OS
The best countermeasure for an OS that has reached the end of its support period is to upgrade to the latest version.
For Windows OS and macOS, it is often possible to upgrade to the latest version for free, so first check if an upgrade is possible.
Especially for companies, continuing to use systems with insufficient security measures poses serious risks such as customer information leaks.
This could also lead to legal liability, such as claims for damages from business partners.
![]() Ken
Ken
About Windows OS
Let’s take a closer look at the support periods for Windows OS.
Windows OS Support Period List
The support periods for each Windows OS are as follows.
| Windows OS | Release | Mainstream Support End Date | Extended Support End Date |
|---|---|---|---|
| Windows 11 | October 5, 2021 | October 5, 2026 | October 5, 2031 |
| Windows 10 | July 29, 2015 | October 14, 2025 | October 14, 2025 |
| Windows 8.1 | October 17, 2013 | January 10, 2023 | January 10, 2023 |
| Windows 8 | October 26, 2012 | January 9, 2018 | January 10, 2023 |
| Windows 7 | October 22, 2009 | January 14, 2020 | January 14, 2023 |
| Windows Vista | January 30, 2007 | April 10, 2012 | April 11, 2017 |
| Windows XP | October 25, 2001 | April 14, 2009 | April 8, 2014 |
Generally, Microsoft provides about 10 years of support for each Windows version after its release.
This support period is divided into two phases: mainstream support and extended support.
Mainstream support ends first, followed by the end of extended support. Once extended support ends, vulnerabilities and bug fixes are no longer provided, leaving the system unprotected.
Mainstream Support Period
Mainstream support is when Microsoft provides updates such as new features, security patches, and bug fixes.
This period lasts at least five years from the release, during which users receive the latest features and security updates.
After mainstream support ends, the OS enters the extended support period, during which only security updates are provided. No new features or bug fixes are released during this time.
Extended Support Period
During extended support, Microsoft provides limited support such as security patches and important fixes.
This period also lasts at least five years, during which security updates are provided.
However, new features and free support available during mainstream support are not provided.
To operate systems safely, both companies and individuals should keep track of the extended support end date and consider migrating to a new OS before it expires.
How to Check Your Current Version
To find out when your extended support ends, here is how to check which version of Windows OS is currently being used.
- Right-click the Windows icon at the bottom left
- Left-click [System]
- Check [Edition] under [Windows Specifications]
A screen like this will appear.
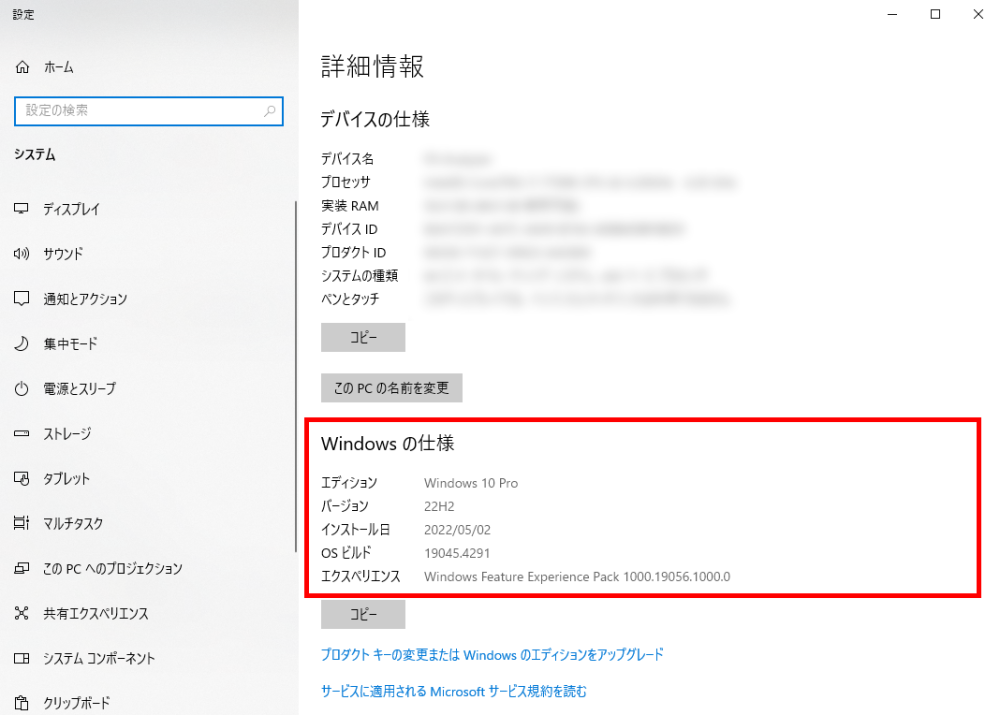
Here, you should see something like Windows 10 or Windows 11 listed.
Examples of Security Incidents After End of Support
Here are some specific examples of security incidents that occurred because security updates were not provided after the support period ended.
It is hoped that these examples will help readers understand the risks of continuing to use unsupported OS versions and the importance of upgrading.
*Currently, security patches have been distributed, so if you are using a version of Windows with the latest updates or have performed Windows Update, there is no problem.
TCP/IP Vulnerability
In February 2021, Microsoft announced that there were several critical vulnerabilities in the TCP/IP stack of Windows 7 and later versions (CVE-2021-24074, CVE-2021-24094, CVE-2021-24086).
These vulnerabilities allowed remote attackers to execute arbitrary code and perform denial-of-service (DoS) attacks, potentially causing system downtime or data leaks.
Windows OS versions from Windows 7 onward were affected, and systems without the patch applied were at high risk.
If a remote code execution vulnerability is exploited, attackers can perform any operation on the system.
This allows for data theft, tampering, destruction, and can cause the system to crash, severely impacting business operations.
Attacks exploiting this vulnerability have been reported, especially targeted attacks on company and organization networks.
Attackers can use these vulnerabilities to infiltrate systems, steal or destroy information, and disrupt services.
*Arbitrary code means that attackers can take control of the system and run any program or script they choose.
Specifically, the following actions are possible:
- Installing malware: Attackers can install malicious software such as viruses, ransomware, or spyware on the system.
- Data theft: Attackers can run programs to steal important data or personal information from the system.
- System destruction: Attackers can delete or corrupt system files and data.
- Remote access: Attackers can operate the system remotely and use it as a base for further attacks.
For example, with a remote code execution (RCE) vulnerability, attackers can send specific network packets or files to the target system and trigger their chosen code to run.
Such attacks often result in attackers gaining administrator privileges, allowing them to control the entire system .
As someone who writes programs, it is clear that if code can be executed, anything can be done inside the computer, such as destroying data or sending information to a specific server.
WannaCry Ransomware Attack
The WannaCry ransomware attack occurred in May 2017, infecting computer systems worldwide by exploiting a known Windows vulnerability.
This attack had a major impact, especially on systems such as Windows XP and Windows Server 2003, which were no longer supported.
The vulnerability existed in the Windows Server Message Block (SMB) protocol, allowing attackers to execute code remotely.
This attack caused widespread disruption globally, particularly affecting the healthcare, telecommunications, and logistics sectors.
Systems without security patches were especially affected.
Attackers used exploits (methods or tools for abusing vulnerabilities) to infiltrate vulnerable systems.
After infiltration, WannaCry ransomware self-replicated and spread to other vulnerable systems on the network.
WannaCry encrypted files on infected systems and displayed a message demanding ransom in Bitcoin to restore them.
If payment was not made, the ransom amount increased after a certain period, and eventually, it threatened that files would be lost permanently.
This attack infected about 230,000 computers in over 150 countries.
Major damage was suffered by medical institutions, telecommunications companies, and logistics companies. In the UK, many hospitals and clinics were attacked.
Access to patient records was restricted, and surgeries and treatments were delayed.
Major companies such as FedEx (a US delivery and logistics company), Renault (a French car manufacturer), and Telefonica (a major telecommunications company based in Spain) were also attacked, suffering serious impacts such as production line shutdowns and communication service interruptions.
Microsoft released a patch (MS17-010) in March 2017 to fix the vulnerability, including for unsupported OS versions as an exception, but many systems were not updated and were affected by this attack.
![]() Ken
Ken
BlueKeep
BlueKeep (CVE-2019-0708) is a critical vulnerability in the Remote Desktop Services of older versions such as Windows 7 and Windows Server 2008.
This vulnerability allows attackers to execute arbitrary code remotely.
Specifically, attackers can access the system through the Remote Desktop Protocol without authentication and take full control of the system.
Full access to the system is possible, and the infection can spread to other computers on the network.
Microsoft has provided a patch for this vulnerability. Exceptionally, patches were also provided for unsupported systems (Windows XP and Windows Server 2003).
After this vulnerability was disclosed in May 2019, many security experts called for patches to be applied before attacks occurred.
However, since unpatched systems still exist, attacks using BlueKeep have been confirmed.
As a result, there have been cases where attackers installed malware and conducted further attacks or stole data.
Summary: Do Not Use Unsupported OS Versions to Prevent Security Incidents! Upgrade to the Latest OS Quickly
Operating systems are updated daily by developers to make them more convenient and comfortable for users.
For example, updates include adding or improving features, enhancing performance, improving the user interface, distributing security patches, fixing bugs, and updating compatibility.
These updates are provided within the support period, so once the support period ends, such updates are no longer available.
In particular, if security patches are not updated, vulnerabilities and security holes discovered after that point will remain unaddressed.
To avoid this, it is important not to use unsupported OS versions and to upgrade to the latest OS.
Here are the key points once again.
- Even after the support period ends, computers do not become unusable
- When the OS support period ends, security risks increase
- The best countermeasure is to upgrade to the latest OS as soon as possible
- Ideally, upgrade before the support period ends
- For companies, this can lead to serious security incidents such as customer information leaks
This article also explains the overall aspects of operating systems, such as types of OS, versions and editions, types of installation media, and license types.
≫ Related article: How to Choose an OS for a Custom PC [Performance / Features / Compatibility]
Select PC parts and online stores to instantly generate an estimate, check compatibility, and calculate power requirements. You can save up to five different builds, making it easy to try out multiple configurations.
≫ Tool:PC Parts Estimation & Compatibility Check Tool
 ZisaLog: Beginner’s Guide to Building a Custom PC
ZisaLog: Beginner’s Guide to Building a Custom PC